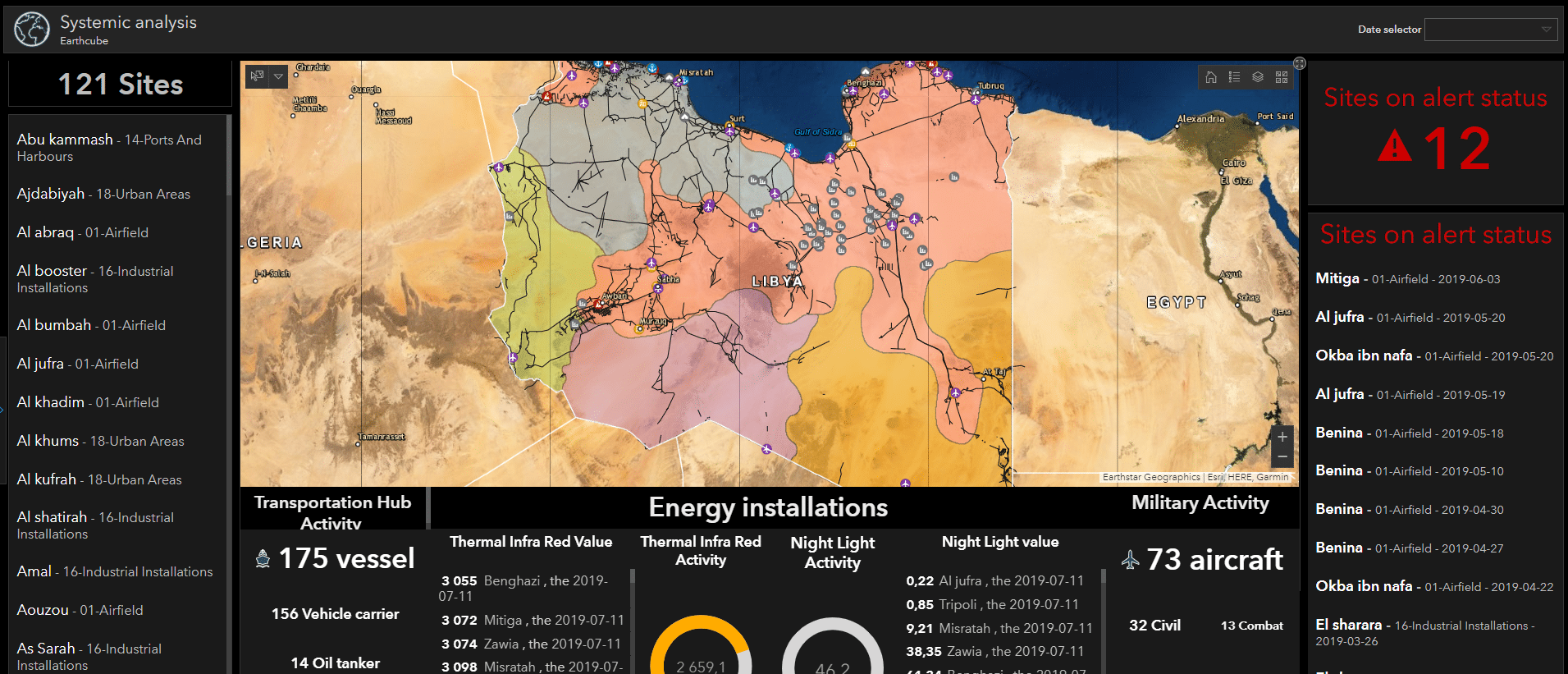
Ttps Military Acronym - As I read various information security reports, blogs, and tweets, I often see "TTP" being used to describe a myriad of things related to information security (such as testing, tools, processes, programs, etc.). Although TTP is a commonly used acronym, it is often not what it really means: Strategies, Techniques and Processes. In this post, I will discuss my interpretation of TTP (based on DoD doctrine) and explain why I believe you should use TTP!
Tactics, techniques and procedures are specific terms originating from the Department of Defense and used over the years to describe military operations. Joint Publication 1-02,
Ttps Military Acronym

Now that we have the "official" definitions, what do they really mean? I like to think of these as a series of attributes, from the broadest (tactics) to the most specific (processes). To help clarify what these actually mean in practice, I'll go ahead and explain what each term actually means. Additionally, I will use the metaphor of "owning a car" to help describe each of these terms.
U.s. Military Lingo: The (almost) Definitive Guide
Strategies are high-level ideas that contain limited concrete information about how things should be done. Usually used for planning and/or tracking, there are no specific instructions or guidelines, just simple guidelines useful for high-level ideas to ensure that everything needed is part of a larger whole.
To use the analogy of car ownership, there are many "tricks" involved in owning a car, such as providing fuel, cleaning and preventive maintenance. Each of these can be considered a "trick" involved in owning a car. For the purposes of this example, we will focus on "preventive maintenance" as the chosen strategy to dive deeper into.
The high level view of the techniques and the very specific details of the processes (discussed below) create a gray area. They include actions that are expected to be completed, but without specific instructions (ie, non-specific) on how to complete that action. This usually results from identifying the tasks that need to be completed, but without micromanaging how to complete the task.
To continue with the car analogy, if the chosen strategy is "preventive maintenance", there will be many different techniques that can be used to achieve that strategy, such as changing the oil, rotating the tires, braking. Changing etc. These techniques outline the general However, the tasks to be completed do not provide specific instructions on how to complete them. We will select the "oil change" we are interested in and use it to discuss the procedures.
Training Prepares Soldiers For Afghan Equipment Retrograde Mission
Procedures are specific detailed instructions and/or guidelines for completing a task. Procedures include all the necessary steps involved in performing a particular task, but without the high-level thinking or background as to why the task is being performed. The priority for the procedures is to provide complete detailed instructions so that the work can be completed correctly by anyone qualified to follow the instructions.
To complete our car analogy, the procedures for performing the "oil change" technique will be specific to the car being built. It will contain all the information about change frequency, oil type, filter type, drain plug condition, tools needed, etc. The procedures should be such that anyone (well, almost anyone) can perform the described task. Using these guidelines.
Presenting strategies, techniques and processes as a hierarchy can help visualize the relationships between them. It will be necessary to use one or more techniques to achieve the desired strategies. One or more procedures will need to be followed to complete the necessary techniques. What distinguishes "advanced" actors from others is their ability to implement new technology or sophisticated processes that cannot be easily imitated by others, even though their strategies are often the same as others.

While TTP is used to describe conventional warfare, it can also be very useful in describing cyber security. Fortunately, the MITER ATT&CK matrix is already designed in a way that uses this framework and provides an excellent single resource for security-based TTPs.
Russian Offensive Campaign Assessment, April 20
The column headings represent the different high-level tactics (highlighted in red) that an attacker uses as part of the cyber attack cycle. The individual entries in the matrix under Strategies represent techniques (highlighted in green). As we discussed earlier, there are many techniques listed for each strategy. When you click on any technique, it will take you to a page with additional details about the technique, including examples of actual use by malicious actors. These examples illustrate the procedures used and provide a detailed analysis of the exact actions taken and resources used. Processes can also be seen as specific hashes or precise tools and command lines used for a specific malicious activity. MITER ATT&CK provides an easily accessible TTP failure regarding computer security.
For example, when an attacker needs to access computers or network resources that are not at their home base, they must employ a lateral movement strategy. A popular technique is to use the built-in Windows administrative shares, C$ and ADMIN$, as writable directories on the remote computer. One procedure for implementing this technique might be to use the SysInternals PsExec utility, which creates an executable binary, copies it to a Windows administrator, and starts a service from that partition. Blocking the SysInternals PsExec utility will not completely remove the risk from the Windows Admin Share technique; An attacker can simply use a different process, ie
Or the PowerShell cmdlet Invoke-PsExec. Understanding the nature of the attack and defensive countermeasures is important when evaluating the effectiveness of security controls.
Other than trying to clarify the use of "TTP", why does any of this old military jargon matter in today's computer-driven world? In fact, this approach to understanding malicious activity will make you a better attacker or defender. The ability to decompose complex attacks into TTP will help make it easier to detect or replicate attacks.
Ac72062 2017 Afmcommand Pdf
Understanding the various strategies involved in information security will help plan for any areas of deficiency in your personal experience of the corporate environment and focus efforts where you may currently lack knowledge/coverage. For example, the "reckless breach" mindset is a recognition that effective cybersecurity must recognize other tactics used by attackers rather than focusing solely on preventing the initial compromise. This high-level view will help prevent an oversight in any part of the security program.
It is also very important to understand the difference between techniques and processes. Many network security tools and threat intelligence feeds focus on the specific processes used by the actor (such as tool hashes, filenames, and C2 domains/IPs) rather than the technology being used. Sometimes, the security community will label something as a new technology, when it should be called a new process for an existing technology. Knowing the underlying technology and being able to adapt specific procedures will make you a better operator, no matter what role you play.
As the old saying goes, "Give a man a fish and you feed him for a day." Teach a man to fish and you feed him for life.” It's like focusing on hash and specific IP address fragility indicators). it may temporarily satisfy your needs, but the effect will be short-lived. Teaching the fish focuses on the technique used, by attacking. Understanding the technology and behavior involved and creating flexible countermeasures that will work even if an attacker adapts or creates new processes.
I hope this post was helpful in clarifying the differences between strategies, techniques, and processes, as well as highlighting the benefits of understanding each term. What is military doctrine? This is a simple question. But I asked cadets, peers and a few willing superiors, and the range of responses is surprisingly wide. I also hear the word "principle" is used in many different ways like "whoah", depending on the context, tone and inflection of the voice, and what the recipient means is "yes", "hard", "let's go" can to be everything. ,” to “I really don't like you.” This should not be the case with doctrine and we (military professionals) must address this lack of clarity.
Ryan Stillions: On Ttps
A quote from a German officer during World War II illustrates the persistence of the Army's ambivalence toward the doctrine: "One serious problem in planning a battle against American doctrine is that the Americans neither read their manuals nor feel an obligation to follow their principles. Although our lack of study of doctrine is a separate topic, this quote opens up a conversation about the importance of doctrine in our professional military education.
The first step in learning a theory is to understand what it is. To find the "official" definition of the doctrine, I turned to the Siddhanta (pun intended). Interestingly, the 2008 edition of Field Manual 3-0: Operations had an appendix titled "The Role of Doctrine." The manual it replaced
Sog acronym military, fod acronym military, military acronym list, roe military acronym, pcs military acronym, rto military acronym, military acronym, jag acronym military, acronym military finder, obe acronym military, peo acronym military, pj military acronym
0 Comments